Preliminary configuration
Configuration of security settings
The SSL standard, allowing access to sites with an encrypted connection (protocol HTTPS) is disabled by default in recent versions of Firefox.
The supported versions of Firefox are specified
here
The standards supported by default are: TLS 1.0 to TLS 1.2.
In case of problems, thank you to notify the issue to RTE’s Hotline (
here).
Adding the smart card to the security devices of Firefox
Mozilla Firefox does not automatically take into account the smart card reader.
It is necessary to add manually in Firefox the smart card reader driver in the considered security devices.
To do this, insert you smart card in the reader.
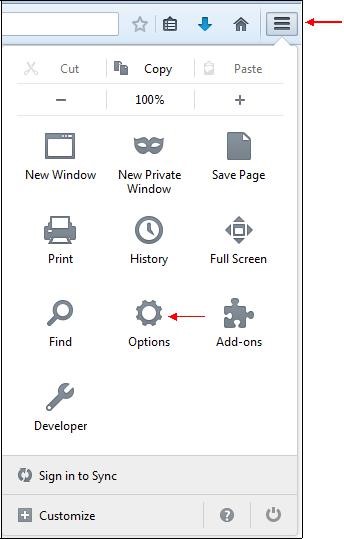
Then go in the menu "
Tools" at the top right of the Mozilla Firefox window, then click on the
"Options" icon.
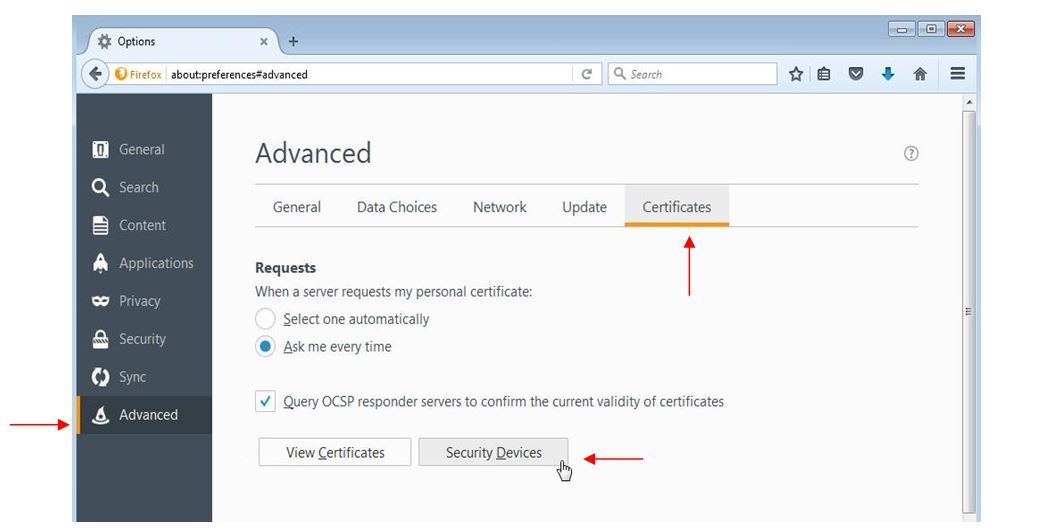
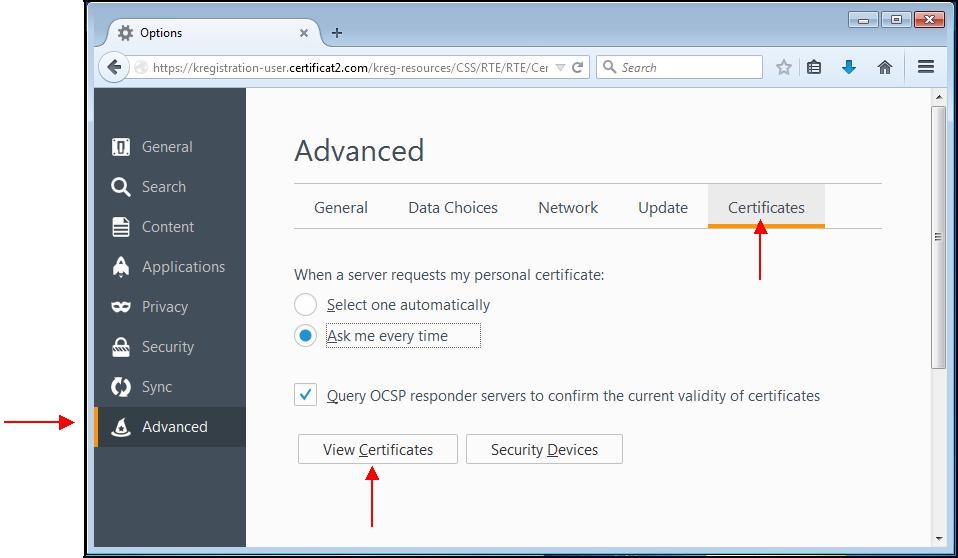
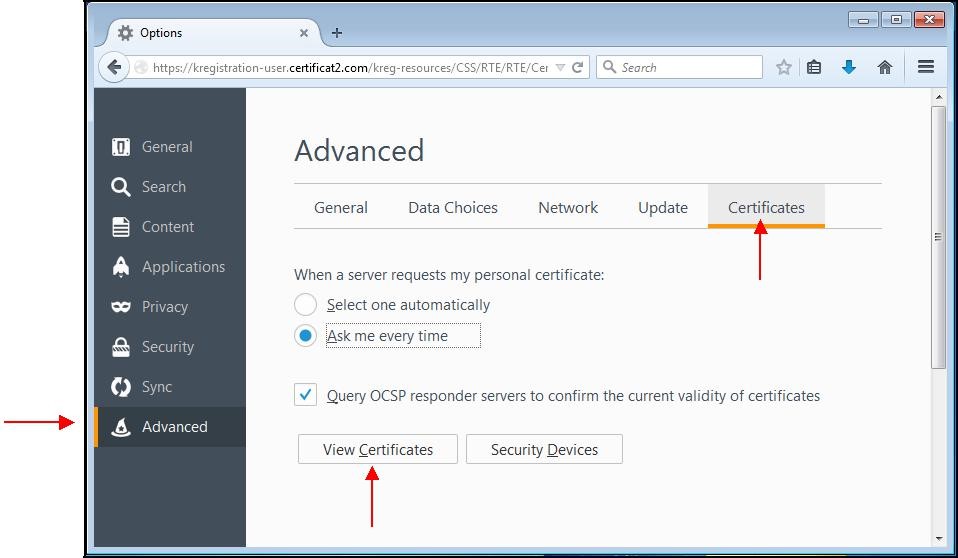
A window appears. Choose the "
Advanced" tab, then the subcategory "
Certificates".
It is necessary to add the smart card reader driver so that Firefox can take into account the smart card. To do this, click "
Security Devices".
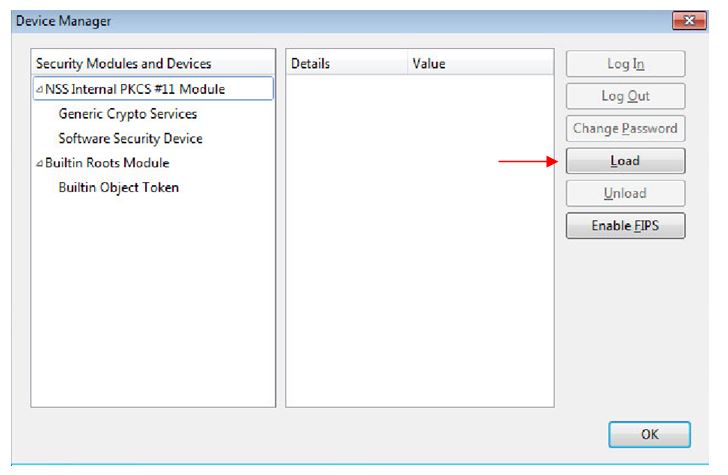
The following window appears.
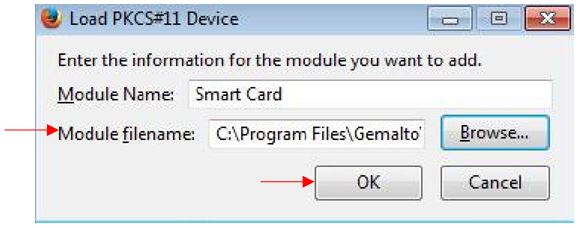
Click "
Load". Another window appears as described below:
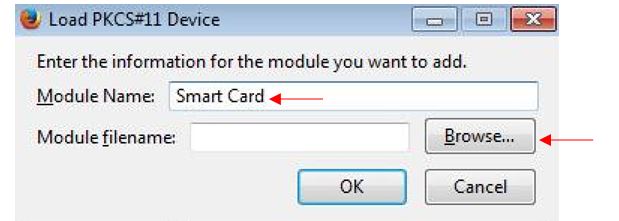
Give the module a name, for example "
Smart Card".
Then click "
Browse".
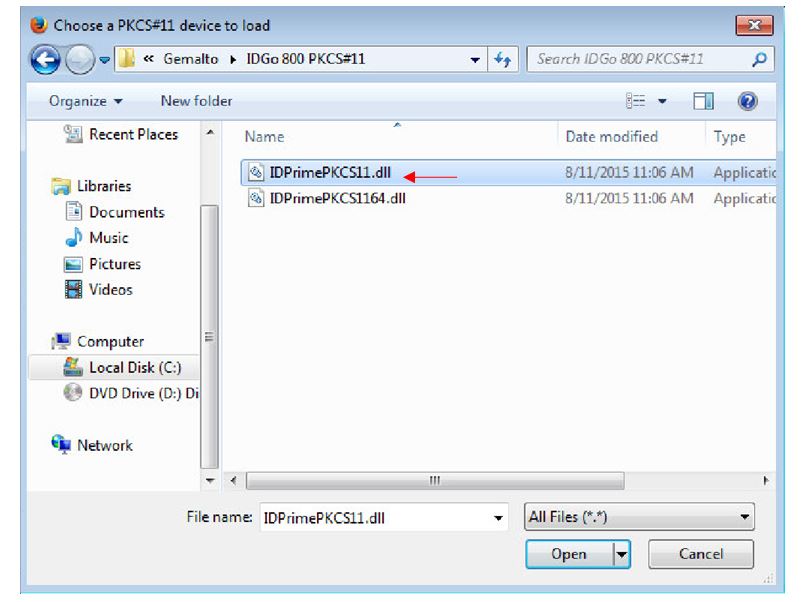
Browse your Gemalto software installation folder (for example
C:\Program Files\Gemalto\IDGo 800 PKCS#11\IDPrimePKCS11.dll) to find the file named
"
IDPrimePKCS11.dll".
Select the "
IDPrimePKCS11.dll" file, then click "
Open".
The following window appears. Click "
Ok".
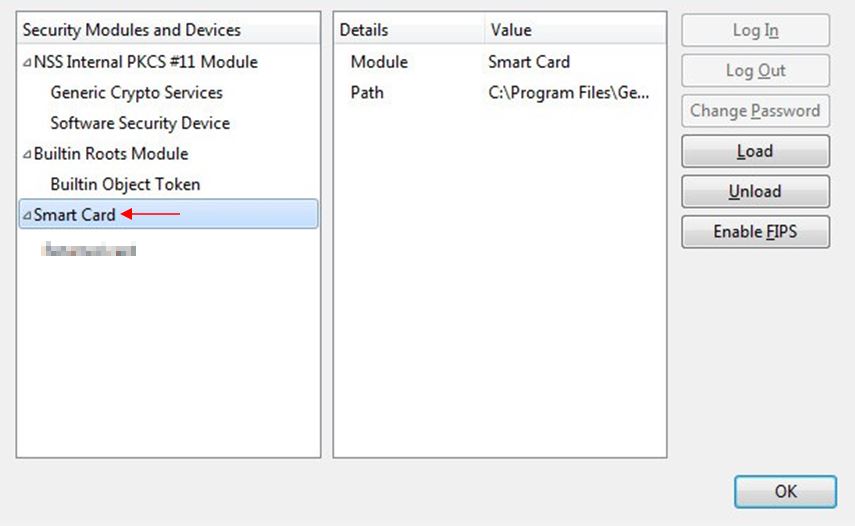
The smart card driver has been added to the list of Security Devices taken into account by Firefox. Click
"Ok".
Installing RTE’s CAs certificates
Download and install
RTE Historical Certification Authority
This CA is the Historical CA of RTE, dealing with 2048 bit keys. This CA is necessary to ensure the cohabitation between the former and the latter PKIs.
RTE Historical CA certificate must now be installed in your browser so that it is recognized as a trusted Certificate Authority.
To do so, please go to the following address:
IMPORTANTE NOTE
It is imperative to respect the case (upper / lower case) of the site’s address.
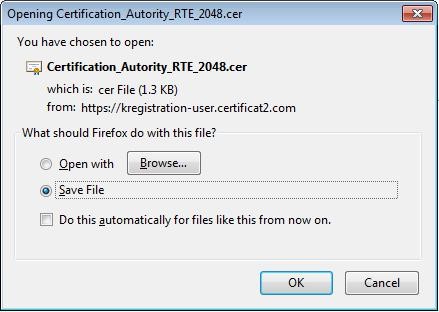
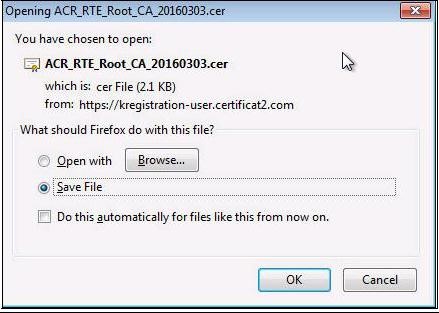
The following pop-up appears, in order to download the certificate,:
Select "
Save file" then click "
OK".
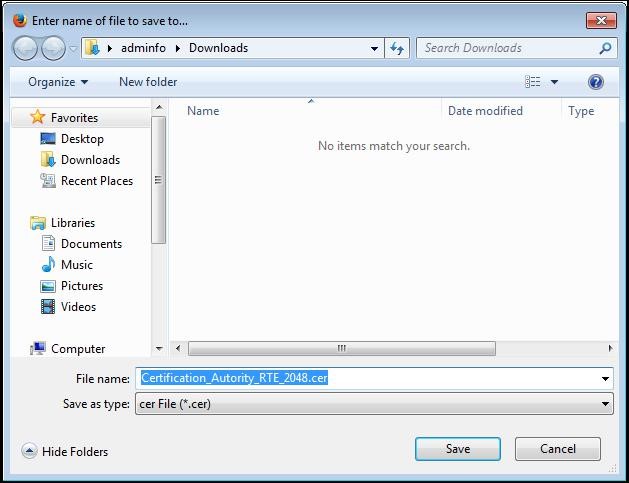
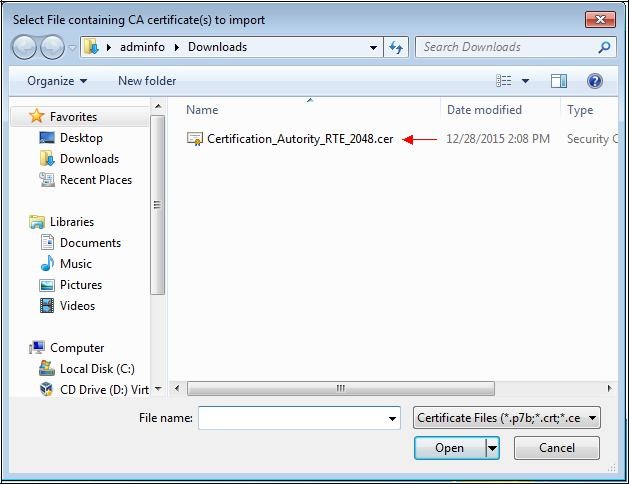
A location to save the file
"Certification_Autority_RTE_2048.cer" will eventually be requested.
Once the file is downloaded, click the menu "
Tools" in the right corner of the window then click the icon "
Options":
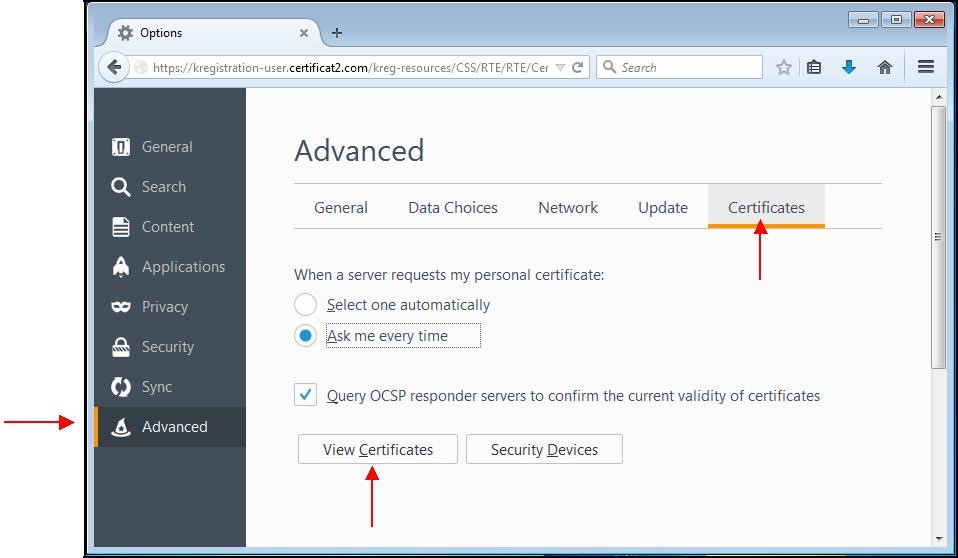
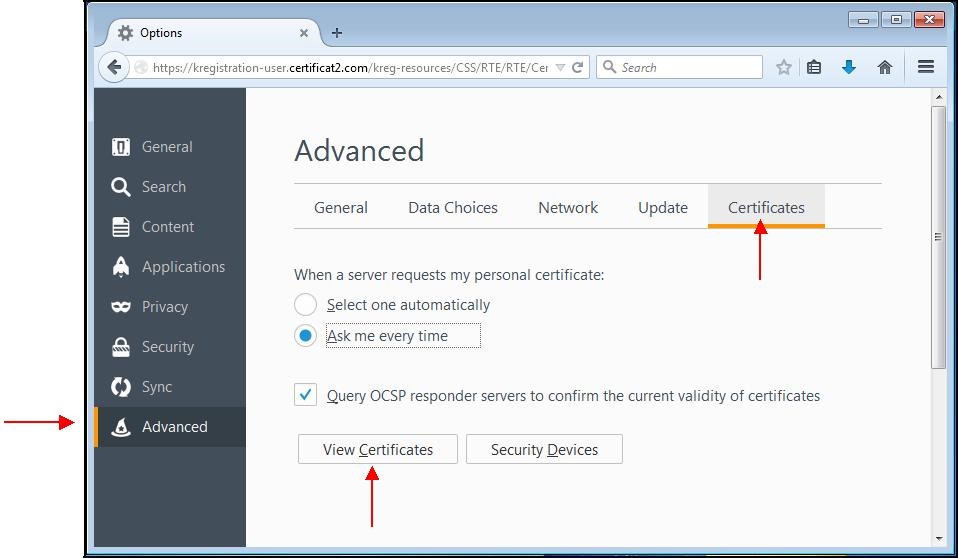
A window appears. Choose the "
Advanced" tab then the subcategory "
Certificates".
Click the "
View certificates" button.
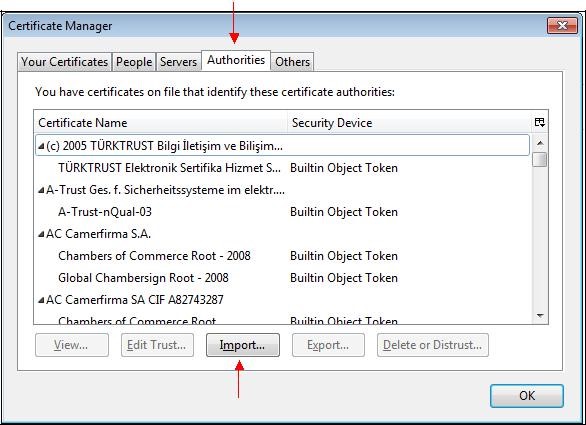
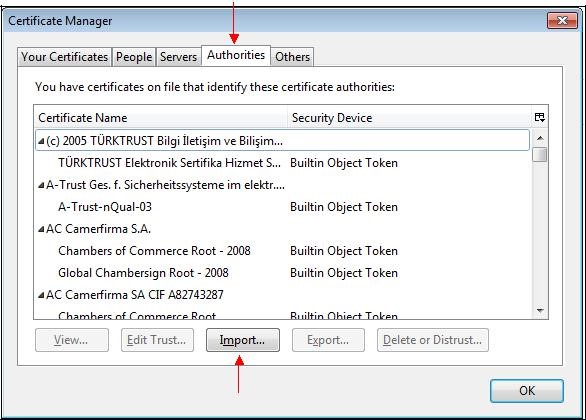
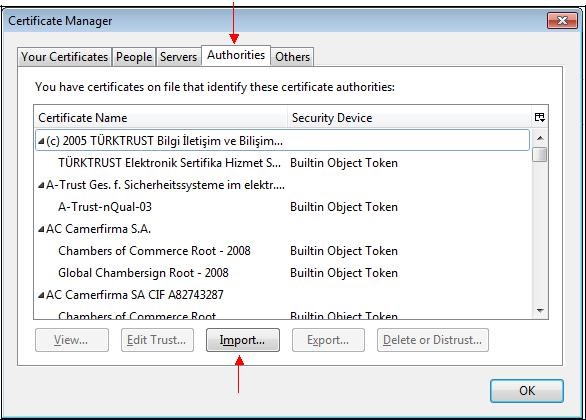
Select the "
Authorities" tab and click "
Import…".
Select the previously saved file.
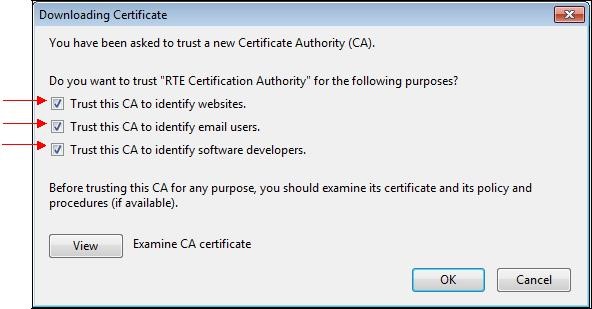
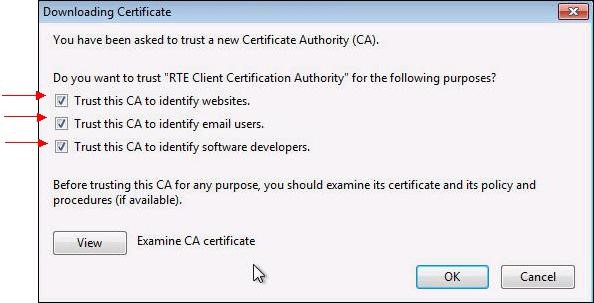
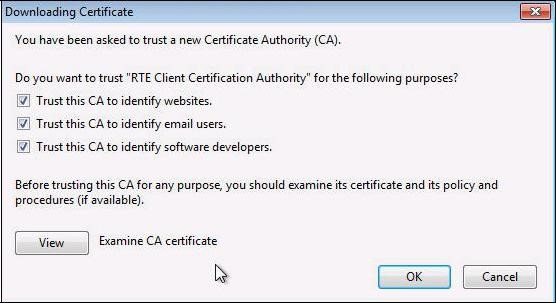
A dialog box is displayed, in which you must select the three check boxes "
Trust this CA to identify [...]" to trust RTE Historical CA.
Click "
View" to check that the certificate you just install is RTE Historical CA’s certificate:
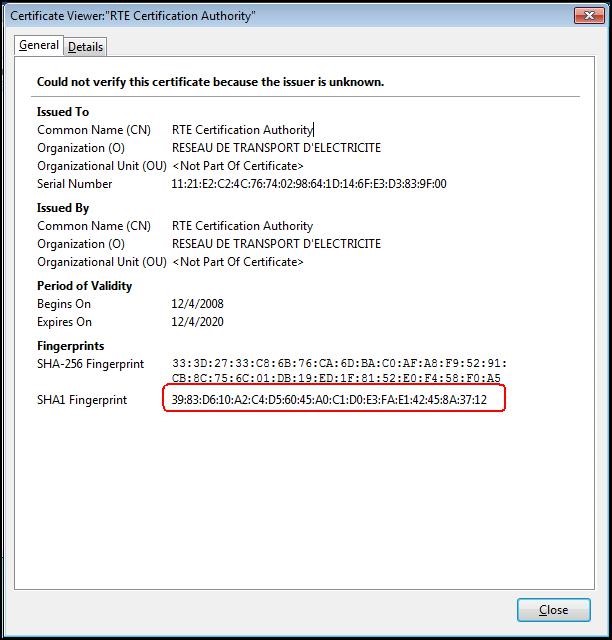
To ensure that you have downloaded the real RTE Historical CA's certificate, check carefully that the "
SHA1" hash displayed is identical to the one shown below.
Digital hash of the certificate "RTE Certification Authority" "SHA1"
"SHA1" 39:83:D6:10:A2:C4:D5:60:45:A0:C1:D0:E3:FA:E1:42:45:8A:37:12
If this is not the case: click "
Close" to go back to the precedent window and click "
Cancel" then call RTE’s Hotline (
here).
If, after verification, the hash of the certificate that you imported matches the "
SHA1" hash above,
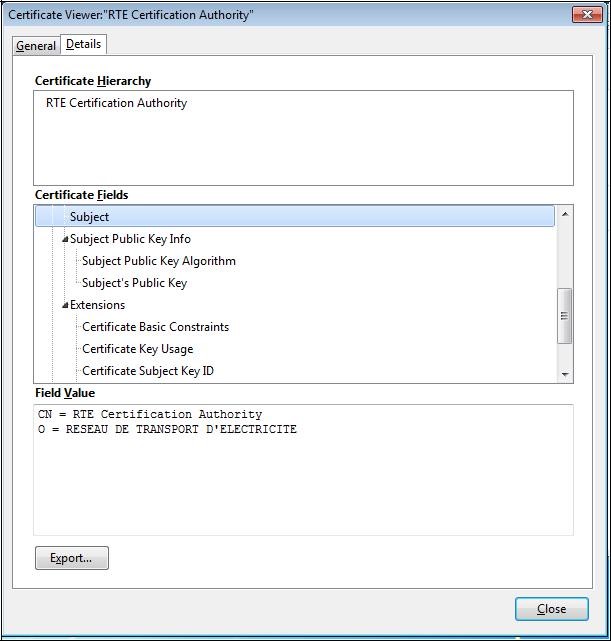
it is possible to consult the details of the certificate by clicking on the "
Details" tab:
By clicking on the "
Close" button, you return to the initial window.
Click "
OK". RTE Historical CA certificate is now installed in the certificate store of Mozilla Firefox
RTE Root Certification Authority
This CA is the new Root CA of RTE, dealing with 4096 bit keys. This CA is necessary to ensure the validation of the chain of trust.
RTE Root CA certificate must now be installed in your browser.
To do so, please go to the following address:
IMPORTANTE NOTE
It is imperative to respect the case (upper / lower case) of the site’s address.
The following pop-up, in order to download the certificate, appears:
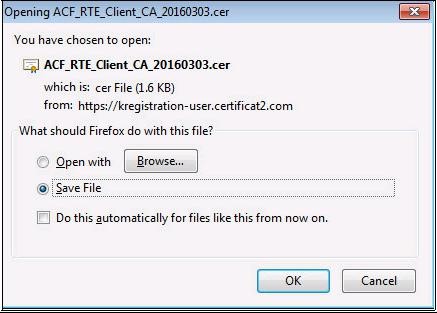
Select "
Save file" then click "
OK".
A location to save the file "ACR_RTE_Root_CA_20160303.cer" will eventually be requested.
Once the file is downloaded, click the menu "
Tools" in the right corner of the window then click the icon "
Options":
A window appears. Choose the "
Advanced" tab then the subcategory "
Certificates".
Click the "
View certificates" button.
Select the "
Authorities" tab and click "
Import…".
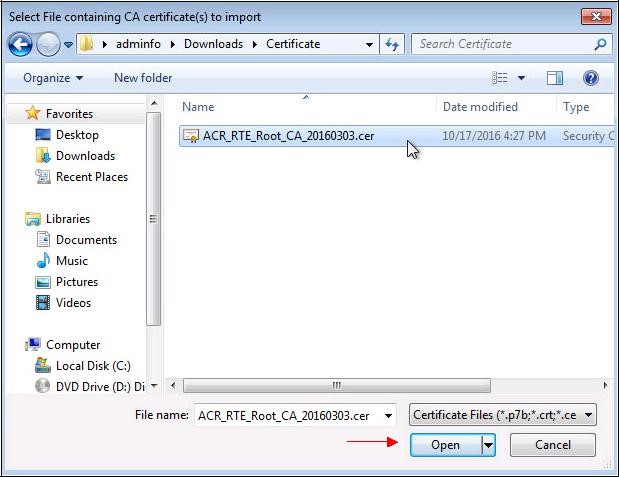
Select the previously saved file.
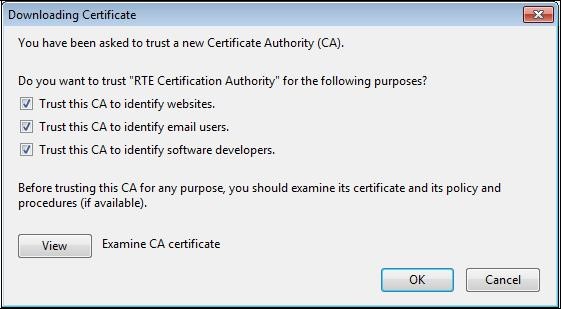
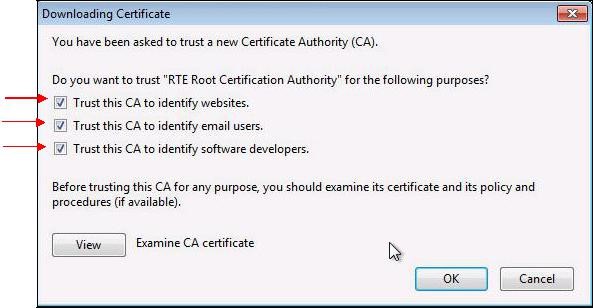
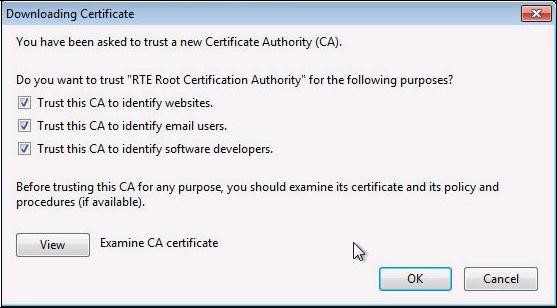
A dialog box is displayed, in which you must select the three check boxes "
Trust this CA to identify [...]" to trust RTE Root CA.
Click "
View" to check that the certificate you just install is RTE Root CA’s certificate:
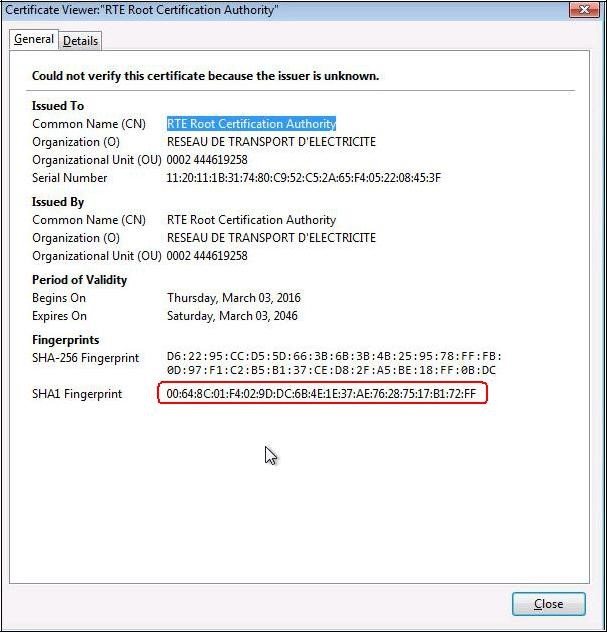
To ensure that you have downloaded the real RTE Root CA's certificate,
check carefully that the "
SHA1" hash displayed is identical to the one shown below.
Digital hash of the certificate "RTE Root Certification Authority"
"SHA1" 00:64:8c:01:f4:02:9d:dc:6b:4e:1e:37:ae:76:28:75:17:b1:72:ff
If this is not the case: click "
Close" to go back to the precedent window and click "
Cancel" then call RTE’s Hotline (
here).
If, after verification, the hash of the certificate that you imported matches the "
SHA1" hash above,
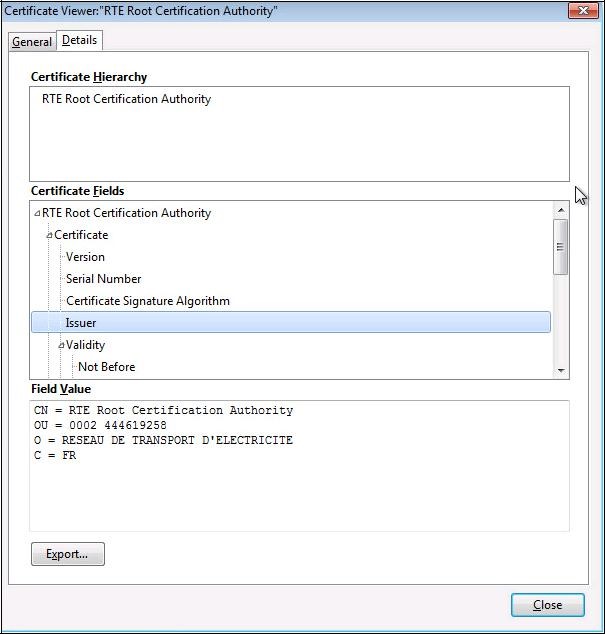
it is possible to consult the details of the certificate by clicking on the "
Details" tab:
By clicking on the "
Close" button, you return to the initial window.
Click "
OK". RTE Root CA certificate is now installed in the certificate store of Mozilla Firefox.
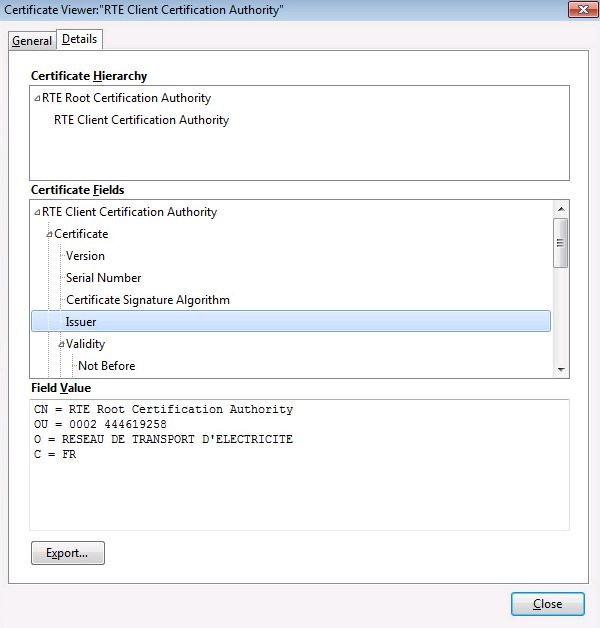
RTE Client Certification Authority
This CA is the new Client CA of RTE, dealing with 4096 bit keys. This CA is necessary to generate the new PKI’s certificates.
RTE Client CA certificate must now be installed in your browser.
To do so, please go to the following address:
IMPORTANTE NOTE
It is imperative to respect the case (upper / lower case) of the site’s address.
The following pop-up, in order to download the certificate, appears:
Select "
Save file" then click "
OK". A location to save the file "
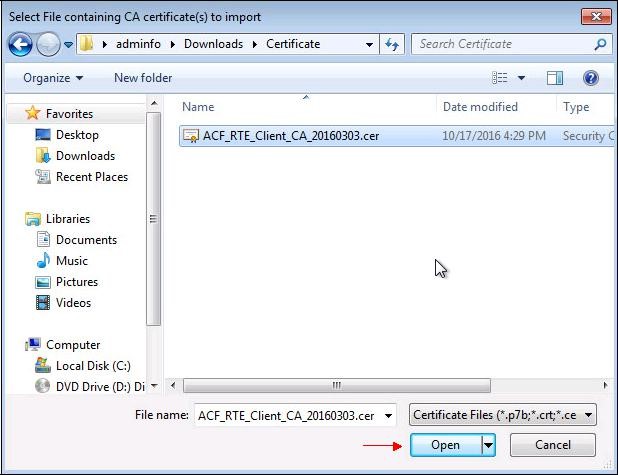
ACF_RTE_Client_CA_20160303.cer" will eventually be requested..
Once the file is downloaded, click the menu "
Tools" in the right corner of the window then click the icon "
Options":
A window appears. Choose the "
Advanced" tab then the subcategory "
Certificates".
Click the "
View certificates" button.
Select the "
Authorities" tab and click "
Import…"
Select the previously saved file.
A dialog box is displayed, in which you must select the three check boxes "
Trust this CA to identify [...]" to trust RTE Client CA.
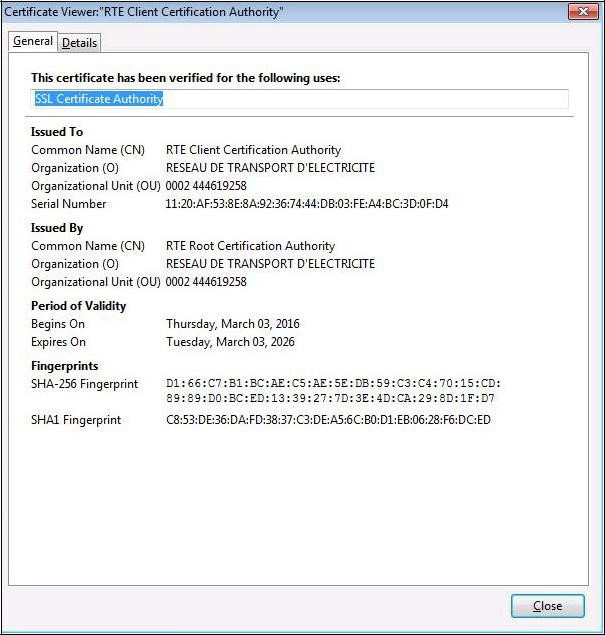
Click "
View" to check that the certificate you just install is RTE Client CA’s certificate:
To ensure that you have downloaded the real RTE Client CA's certificate, check carefully that the "
SHA1" hash displayed is identical to the one shown below.
Digital hash of the certificate "RTE Client Certification Authority"
"SHA1" C8:53:de:36:da:fd:38:37:c3:de:a5:6c:b0:d1:eb:06:28:f6:dc:ed
If this is not the case: click "
Close" to go back to the precedent window and click "
Cancel" then call RTE’s Hotline (
here).
If, after verification, the hash of the certificate that you imported matches the "
SHA1" hash above,
it is possible to consult the details of the certificate by clicking on the
"Details" tab:
By clicking on the "
Close" button, you return to the initial window.
Click
"OK". RTE Client CA certificate is now installed in the certificate store of Mozilla Firefox.
Visualization and verification of RTE CAs certificates
To see the certificates in Mozilla Firefox, click the menu
"Tools" in the right corner of the window then click the icon
"Options":
A window appears. Choose the "
Advanced" tab then the subcategory "
Certificates".
Click the "
View certificates" button.
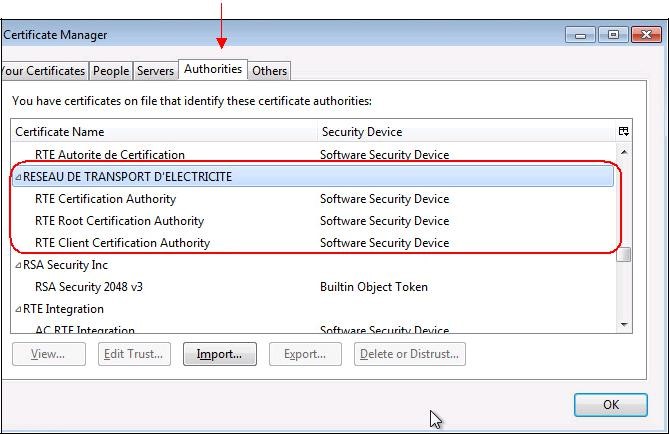
In "
Authorities" tab, you can verify that the certificates you import are register with "
RESEAU DE TRANSPORT D’ELECTRICITE"
organization and are saved on your computer disk ("
Software Security Device").
You can see the content of each certificate by clicking on the certificate and then clicking on "
View".
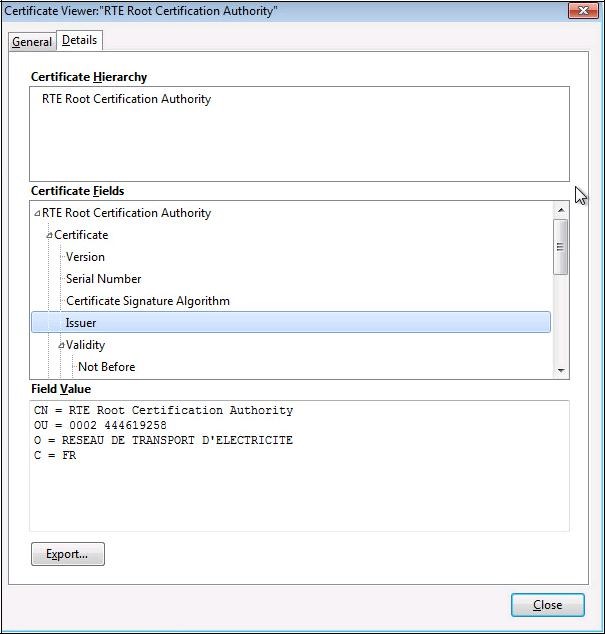
Select "
RTE Certification Authority" and click "
View":
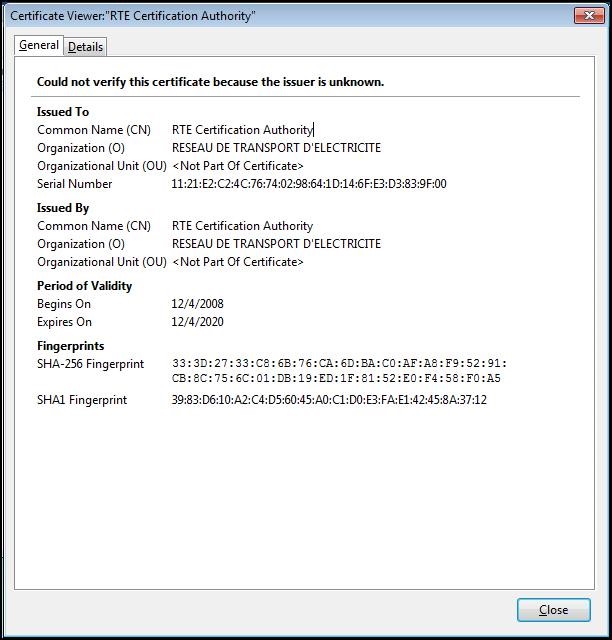
To ensure that you have downloaded the real RTE Historical CA's certificate,
check carefully that the "
SHA1" hash displayed is identical to the one shown below.
Digital hash of the certificate "RTE Certification Authority" "SHA1"
"SHA1" 39:83:D6:10:A2:C4:D5:60:45:A0:C1:D0:E3:FA:E1:42:45:8A:37:12
If this is not the case: click "
Close" to go back to the precedent window and call RTE’s Hotline (
here).
If, after verification, the hash of RTE Historical CA certificate that you imported matches the "
SHA1" hash above,
it is possible to consult the details of the certificate by clicking on the "
Details" tab:
By clicking on the "
Close" button, you return to the initial window.
Select "
RTE Root Certification Authority" and click "
View":
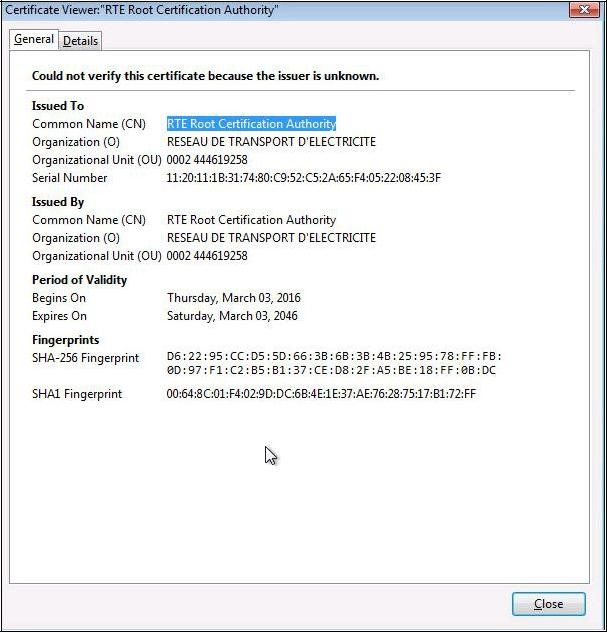
To ensure that you have downloaded the real RTE Root CA's certificate,
check carefully that the "
SHA1" hash displayed is identical to the one shown below.
Digital hash of the certificate "RTE Root Certification Authority" "SHA1"
"SHA1" 00:64:8c:01:f4:02:9d:dc:6b:4e:1e:37:ae:76:28:75:17:b1:72:ff
If this is not the case: click "
Close" to go back to the precedent window and call RTE’s Hotline (
here).
If, after verification, the hash of RTE Root CA certificate that you imported matches the "
SHA1" hash above,
it is possible to consult the details of the certificate by clicking on the "
Details" tab:
By clicking on the "
Close" button, you return to the initial window.
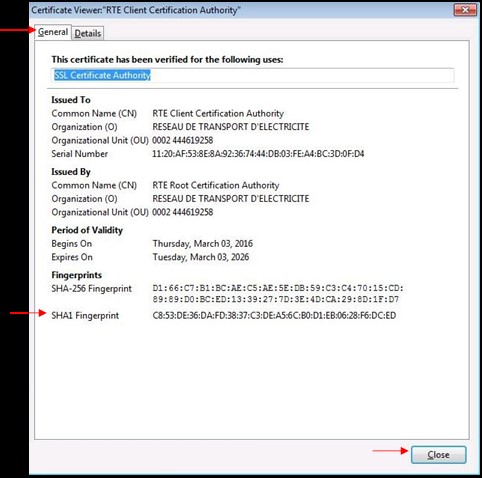
Select "
RTE Client Certification Authority" and click "
View":
To ensure that you have downloaded the real RTE Client CA's certificate,
check carefully that the "
SHA1" hash displayed is identical to the one shown below.
Digital hash of the certificate "RTE Client Certification Authority" "SHA1"
"SHA1" C8:53:de:36:da:fd:38:37:c3:de:a5:6c:b0:d1:eb:06:28:f6:dc:ed
If this is not the case: click "
Close" to go back to the precedent window and call RTE’s Hotline (
here).
If, after verification, the hash of RTE Client CA certificate that you imported matches the "
SHA1" hash above,
it is possible to consult the details of the certificate by clicking on the
"Details" tab:
By clicking on the
"Close" button, you return to the initial window.
Visualization and verification of your smart card certificates
Once the smart card reader driver has been added to Firefox, it is possible to visualize the certificate contained in the smart card.
To do this, insert your smart card in the card reader plugged into your computer’s USB port.
Then get in the
"Tools" menu at the top right of the window, and then click on the
"Options" icon:
Choose the "
Advanced" tab, then the "
Certificates" subcategory.
Click
"View Certificates"
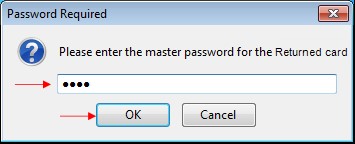
In the window that appears, input your card
PIN code
Click
"OK".
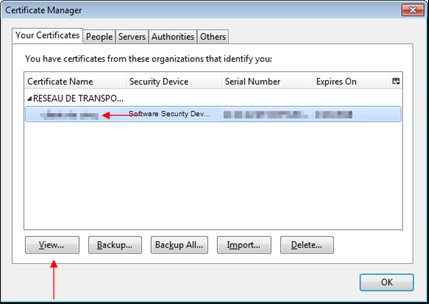
Click on the
"Your Certificates" tab.
You can visualise your certificates by selecting them in the list then by clicking
"View".
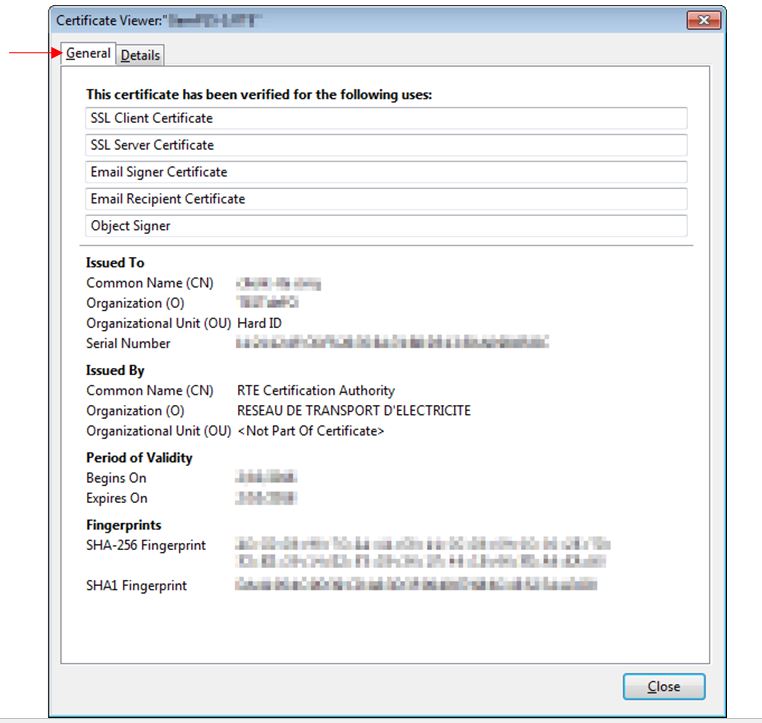
The 1st tab "
General" displays the message
"This certificate has been verified for the following uses".
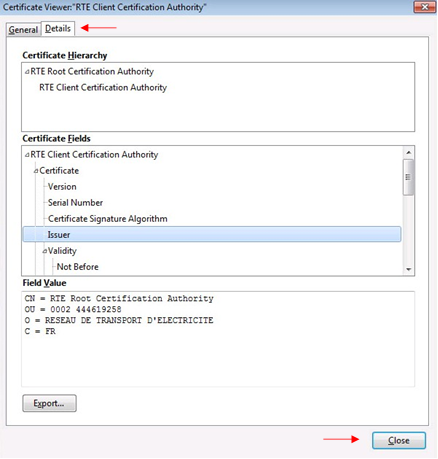
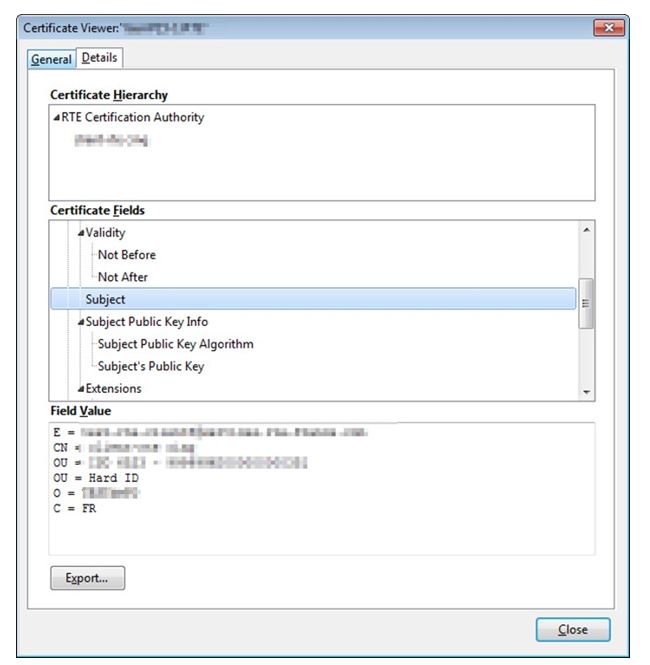
The second tab "
Details" displays the hierarchy of certificates with the RTE CA root certificate.
This ensures that all certificates have been correctly installed, and that all correct usage conditions are brought together.
Using your certificate
Authentication and encryption
Steps to follow
- Insert your smart card,
- Run Firefox, enter the URL to RTE’s application or to "RTE’s customer service portal": https://portail.iservices.rte-france.com
- During the authentication, the browser will ask you to select the certificate to use for authentication then (if it has been defined) the certificate store protection password,
- If multiple certificates are presented, choose the one supplied for the application
you wish to access (use the button "Display certificate" to visualize its content).
Once authentication is completed, all data you send or receive will be encrypted
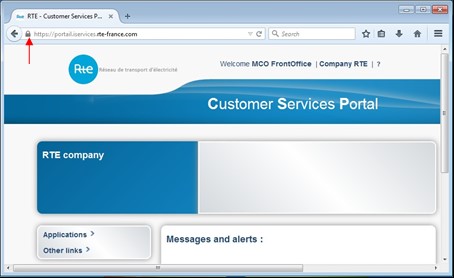
Example of access to an RTE web application
When you access the
"https" homepage, you will be asked to enter your smart card password.
Then, you will be asked to choose your certificate.
Select your certificate from the drop down list entitled
"Choose a certificate to present as identification" then click
"OK"
The home page is then securely displayed, (appearance of the closed padlock on the top left of the URL entry field):